ECB Byte at a Time is a fun crypto attack that doesn’t require any math knowledge. Just an understanding of the systems work and how they interact.
Lets imagine you had some session cookie or token that was constructed like:
AES_ECB(INPUT + SECRET, KEY)
It’s possible to determine SECRET with only control of INPUT! You won’t be able to determine key though. The value of SECRET depends on the target, but SECRETS are usually secret for a reason.
The actual encryption algorithm doesn’t matter either (in this case AES), as long it’s block based and uses ECB.
ECB
Electronic Code Book (ECB) is a mode for block based encryption. Block based encryption algorithms can only take input of a specific size (such as 16 bytes) and output to another specific size.
So if:
- Your input is < 16 bytes, you have to pad to 16 bytes.
- If you input is 16 bytes, perfect! proceed to encryption
- If you input is >16 bytes, you need use the encryption algorithm a couple of times on all the 16 byte blocks.
The mode is how you tie those multiple 16 byte blocks together.
ECB mode is the simplest of the modes, you just take your input that is over 16 bytes and chop it into 16 byte blocks and encrypt each block separately.
For example if we had aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaab.
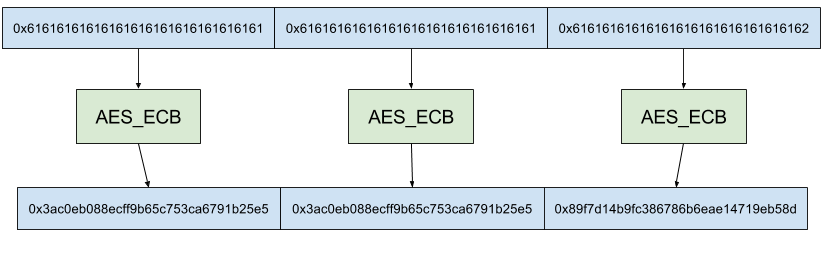
Notice how the first two blocks have the same output because they have the same input (‘a’ * 16).
So if we have two 16 byte blocks with the same input, we’ll get the same output. This is the info leak we’ll be abusing.
The Attack Setup
So how can we use this knowledge to help us?
Lets say we found a website that was generating session cookies based on:
AES_ECB(USERNAME + SECRET, KEY)
And we have the ability to change USERNAME (as long as it’s not already being used) and get the resulting ciphertext. Our goal is to create a valid token for the pre-existing ‘admin’ user.
ECB Byte At a Time
Lets say we crafted a username with 15 ‘a’s.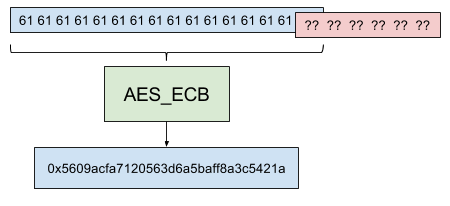
The 16 byte block consist of 15 ‘a’s, and one unknown character from the SECRET.
Now that we know the result of that block, we can iterate through all possible 16 byte blocks starting with 15 ‘a’s. When we find the block that has the same output, we know what the input to that block must have been.

Since the block with the ‘c’ and the unknown secret are equal, we know the first character is ‘c’!
Now we repeat this process with 14 ‘a’s, the ‘c’ from SECRET and the next unknown character. We set our username to aaaaaaaaaaaaa.

And then we iterate through all possible blocks that start with aaaaaaaaaaaaaac.

Since the block with ‘0’ and the unknown character are equal, we know the next character must be zero. So the secret starts with ‘c0’.
Repeat this process till the entire secret is decoded. In this case the secret was c0nrad.
To generate an admin session, simply set your username to ‘admin’+ ‘c0nrad’ + 5pad. And copy the first block as your session secret.
Conclusion
Using ECB at a time we were able to determine the appended secret.
If you want to write your own solver, here’s a demo server you can exploit. code. An example solution can be found here.
Enjoy!
Edit: Correction by reddit/u/oottppxx, mistakenly inserted the ‘c’ manually on letter 2. Use ‘c’ from SECRET.
Nice post, thank you.
Do you know of any CMS/application that uses this encryption scheme or is this only a theoretical approach.
LikeLike
Hey Aimene1905! Personally I’ve only ever used it during CTFs. I originally learned about it from https://cryptopals.com/sets/2/challenges/12. They mention that they see it at least once a year during assessments.
¯\_(ツ)_/¯
LikeLike